Use a Real Commodore 64 as a USB Keyboard for the VICE emulator
22nd March 2025
Exercise your brain with adventure games – Infocom classics and retro computer titles
9th April 2025Bad Update Software Exploit for Xbox 360 – What is it? How does it work? Is it right for you?
Since the Xbox360 was launched in 2005 people have been looking for a way to hack it that doesn’t involve opening up the console, soldering components and attaching NAND memory programmers. In 2025 grimdoomer finally managed to do this with their Bad Update exploit.
This is a software only hypervisor exploit that allows you to run Homebrew code directly on any model of the Xbox 360.
So what does this mean and how does it work. Let’s find out.
What is the Hypervisor?
A hypervisor is a piece of software that manages access to the computer systems resources to make sure that only code that’s authorised to run and interact with the computer is allowed to do so. It’s not part of the actual computer operating system but in effect runs in its own lower-level code layer to manage the operating system and provide base level security.
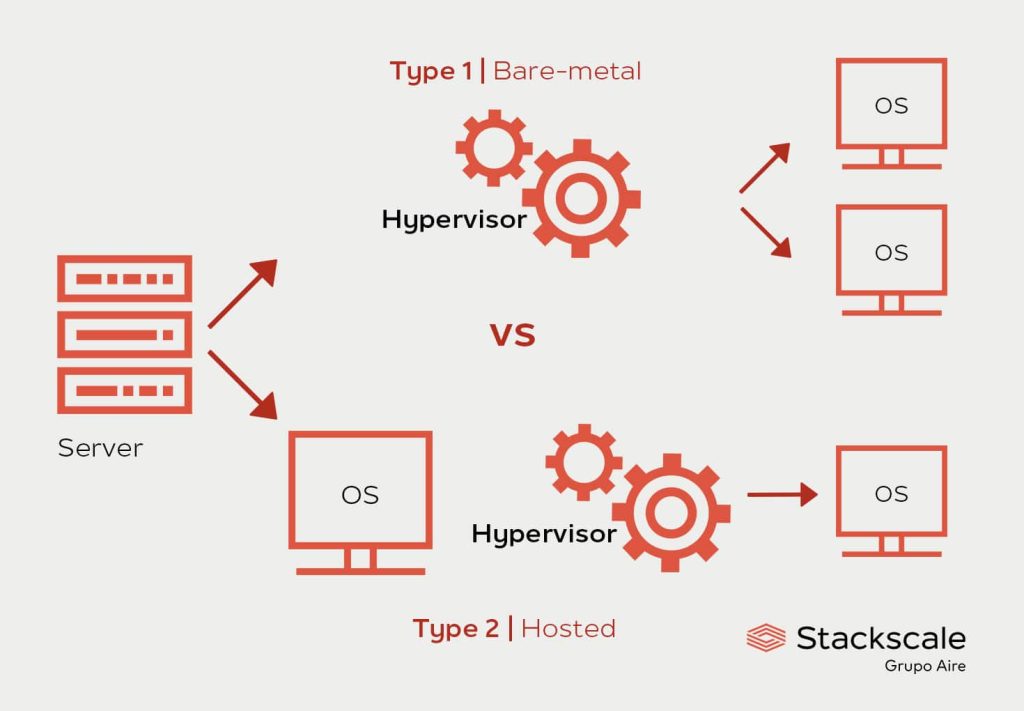
Image from https://www.stackscale.com/blog/hypervisors/
Not all computers use a hypervisor layer. It really comes into its own when there are multiple operating systems trying to share resources such as memory, disks, I/O and so on. Usually this will happen when multiple virtual computers are being run on a single physical computer system. The Hypervisor makes sure that one virtual machine can’t affect any other, either simply to hog resources or, as in the Xbox hypervisor, to inject unauthorised code into the system.
If you’ve ever installed a virtual machine on your Windows or Linux or Mac computer you’ll probably have heard the terms Hyper-V, KVM and so on. These are hypervisors that are installed and/or used by the virtual machine management system. By default your Windows PC doesn’t actually load a hypervisor layer but instead just boots directly into the operating system.
On the Xbox360 this hypervisor layer is built into the actual firmware of the machine. It runs as the machine boots and from then on controls all access to system resources. This boot process is fixed into the Xbox firmware so by the time the console boots up and is able to run application software the hypervisor is already running and in full control. This is why it’s been so hard to get a software exploit working on the Xbox 360.
How Do Exploits Like RGH3 Work?
The hardware exploits such as RGH3 get around the hypervisor’s control by trying to bypass it during the boot sequence or to manipulate it so you can change the way it works.
The RGH, or reset glitch hack, uses some minute timing vulnerabilities in the console’s boot sequence where it runs checks to make sure the code is fully authorised to run. The wire you solder onto the motherboard sends a signal from the Southbridge chip to the main processor to trigger a reset pulse that glitches the processor at just the precise point in the boot process so that it skips some security checks that then allows the code in your modded NAND firmware to run and effectively lock the hypervisor out.
Without this hardware enabled glitch there was no way to break into the boot sequence to get past the hypervisor.
How Does the Bad Update Exploit Work?
So hopefully you can now see the issue that’s prevented people from developing a software only exploit. How do you stop the very secure hypervisor from running after it has already run?
So how does the Bad Update exploit work?
For a full explanation please have a look at grimdoomer’s own explanation.
https://github.com/grimdoomer/Xbox360BadUpdate/wiki/Exploit-Details
The actual explanation of what the vulnerability is, how it works and how they wrote the code to take advantage of it is fully explained on the linked pages. So please do have a look through to get an overview of how it was all put together.
To be honest this level of coding is way beyond me and I really do have the utmost respect for grimdoomer.
So here’s my very superficial level attempt to explain what’s happening.
The Xbox hypervisor is a very well written piece of very secure code. It does lock down pretty much every software process and interaction requiring everything to be fully encrypted and authorised. But there are a few system calls where it does allow small pieces of signed code to be run. Game code can use these system calls to run various updates to the console.
After analysing a whole range of game update payloads, grimdoomer noticed that there was a scenario where the hypervisor could allow custom code to run, but that it needed to be run from encrypted memory.
Working out how to inject the required data into that encrypted memory seems to be the main focus of the exploit.
From what I can gather the hypervisor uses a 10 bit whitening value to encrypt the data. This gives 1024 possible key values. By breaking into the update code at the correct point you can simply use brute force to check all possible combinations of this whitening value to see if you can correctly encrypt your exploit code package so that it will be accepted by the hypervisor.
At this point you have a small block of code that can then cause your full exploit code to be run.
If you do look through the explanations you’ll get the full picture, and there are quite a few more steps to getting control on the console. But I’m not sure I can properly explain what those steps are so I’m going to leave it here.
Basically you run the exploit code as part of a game that exhibits the hackable update process. It then tries to guess the whitening value to allow the exploit code to be injected into the hypervisor system call. When it gets it right you get a hacked console.
Is This a Better Option Than the RGH3 Hack?
With the Xbox 360 the hope has always been to get a software only mod that will work with all models and remove the need to do some quite fiddly soldering to the motherboard along with the NAND reprogramming etc. that goes with the RGH3 style mods.
As grimdoomer themselves states, the Bad Update exploit does offer this software only solution, but it doesn’t replace the hardware mods. They see it as more of a proof that it can be done rather than a fully-fledged solution in itself.
The Bad Update mod is non-persistent. Once you run the hack it will allow you to do most of what you’d be able to do with the RGH3 exploit. But since it’s using code injected into the run time configuration of the console, as soon as you remove the power and reboot the exploit is removed. You have to re run the exploit every time you reboot the machine. As it can take up to 20 minutes for the exact timing conditions to be met once you reboot it’s not as user friendly as the standard mods.
The good part is that it will run on ALL Xbox 360 models. Not all of these can be hard modded so if you’ve got a Winchester motherboard in our console then Bad Update is your only option.
Give It A Go!
So please do give this a go. I’m not planning on using it on my Xbox 360 so please do have a look at MrMario’s installation video if you want full instructions on how to install the exploit.